Details:
Step-by-step configuration instructions for Single Sign-On (SSO) access
to SAP ABAP using IDP (ADFS). We have two scenario, for the configuration of SAML2
Scenario 1:
We have a SAP Web-dispatcher infront of SAP Application Server to access the url.
Scenario 2 :
We are directly accessing the service of SAP Application Server (Without Wed-dispatcher)
Pre-requisite:
SSL need to be configured first before configuring for SAML2 authentication.
Steps:
Activating the Services
1. Goto Transaction SICF, enable below services
/sap/bc/webdynpro/sap/saml2
/sap/public/bc/sec/saml2
/sap/public/bc/sec/cdc_ext_service
/sap/bc/webdynpro/sap/saml2
/sap/public/bc/icf/logoff
/sap/public/bc/sec/saml2
/sap/public/myssocntl
/sap/bc/saml2/idp/sso
/sap/bc/webdynpro/sap/SAML2_IDP
2. On the Maintain Services page, enter one of the service name from the list.
3. Right-click the service in the tree menu view, select Activate Service.
4. Prompt to activate the service, click Yes with tree option.
Enable SAML2 Local Provider Setting
1. Run the transaction SAML2 or open the URL
https://<FQDN>:<ICM_HTTPS_PORT>/sap/bc/webdynpro/sap/saml2?sap-client=100&sap-language=EN
Note : If you want to use webdispatcher then open the SAML2 URL through webdispatcher Url
https://<WEBDISPATCHER_FQDN>:<WEBDISPATCHER_ICM_HTTPS_PORT>/sap/bc/webdynpro/sap/saml2?sap-client=100&sap-language=EN
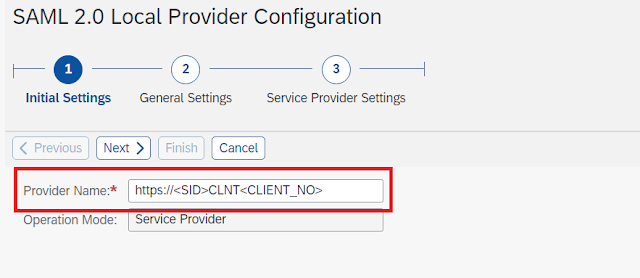
2. Click on Enable SAML2.0 Support and Select "Create SAML 2.0 Local provider".
3. Enter the Provider Name https://<SID>CLNT<CLINET_NO> on Intital setting screen. Click Next.
4. Choose Automatic in Selection Mode on Service Provider Settings and Select Finish.
5. After Click on Finish, it will be redirect you to Configuration Page.
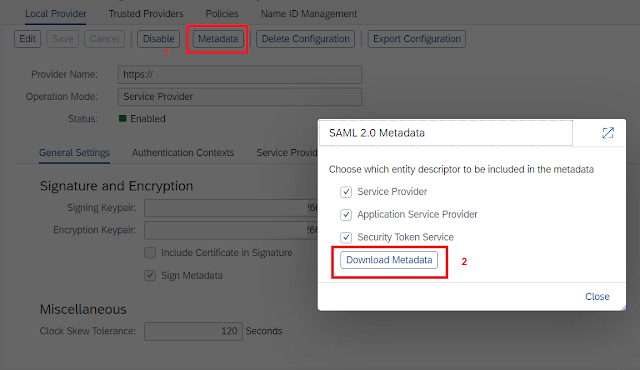
6. Click on Metadata button to get pop-up for the metadata download, then select Download Metadata.Make sure browser pop-up is allowed.
7. Share the Metadata.xml file with the ADFS team, for Relying Party Trust (RPT) in ADFS for the SAP system.
8. Once RPT is done, ADFS will share the federation XML file and certificate which has been used to sign your metadata xml. If in case they do not share the certificate then you can extract the certificate from federation xml.
9. As a next step, open the SAML2 and click on Trusted Providers tab.

10. Select the the Upload Metadata File
11. Upload the federation xml in Metadata file.
12. In the Next Step Metadata Verification, Upload the federation certificate and Click Next
13. In Signature and Encryption Step Choose the Digest Algorithm
14. In Authentication Requirements, Choose the shown and Click Finish.
15. First Click on Edit and then Add then select the Unspecified and then Save the setting.
16. Then Click on Enable to activate the configuration.
17. Goto Transaction SICF , enter the service name or external alias example /sap/bc/ui2/flp and open the service
18. Select Logon Data Tab. Choose the Alternative Logon Procedure and set SAML Logon at 1 and Save.
19 . Test the Service by directly copying the require in browser. In case of any RPT error . Please reach out to ADFS Team.
20. For any other issue access the Security Diagnostic tool using the URL: https://<host>:<port>/sap/bc/webdynpro/sap/sec_diag_tool?sap-client=<sap_client>
21. Log on with a user that has the role SEC_DIAG_TOOL_VIEWER or full administrative rights in the specified ABAP system.
22. In the Name field, enter a description trace file name.
23. Choose the severity of the trace which you needed (ex : Debug, Info, or Error).
24. Click on Start to activate the trace.
25. Reproduce the SAML2 error.
27. Stop the Activated trace, download the generated file. If you need help from SAP then Incident can be raised on component BC-SEC-LGN-SML.
Note :
- Till now due to SAML2/ADFS limitation it is not possible to configure the SAML2 SSO for two different client of the same system.
- If you want to configure the SAML2 SSO for both Webdispatcher and Backend URL then additional share the below URL to ADFS team during RPT.
Example :
https://<Webdispatcher_ALIAS_FQDN>:<WEDB_ICM_PORT>/sap/saml2/sp/acs/<CLINET_NO>
https://<Webdispatcher_Physical_FQDN>:<WEDB_ICM_PORT>/sap/saml2/sp/acs/<CLIENT_NO>
https://<BACKEND_FQDN>:<BACKEND_ICM_PORT>/sap/saml2/sp/acs/<CLIENT_NO>
https://<Webdispatcher_ALIAS_FQDN>:<WEDB_ICM_PORT>/sap/bc/ui2/flp?sap-client=<CLIENT_NO>&sap-language=EN#
https://<Webdispatcher_Physical_FQDN>:<WEDB_ICM_PORT>/sap/bc/ui2/flp?sap-client=<CLIENT_NO>&sap-language=EN#
https://<BACKEND_FQDN>:<BACKEND_ICM_PORT>/sap/bc/ui2/flp?sap-client=<CLIENT_NO>&sap-language=EN#